Security at Democracy Live
For far too long there has been a consensus that voters with disabilities, or serving our country abroad must sacrifice ballot access in order to preserve the security and integrity of the ballot. As described on this page, we believe this is a false and outdated narrative. New technologies developed and proven over the last 15 years by Democracy Live have dramatically increased both ballot access, while substantially increasing security.
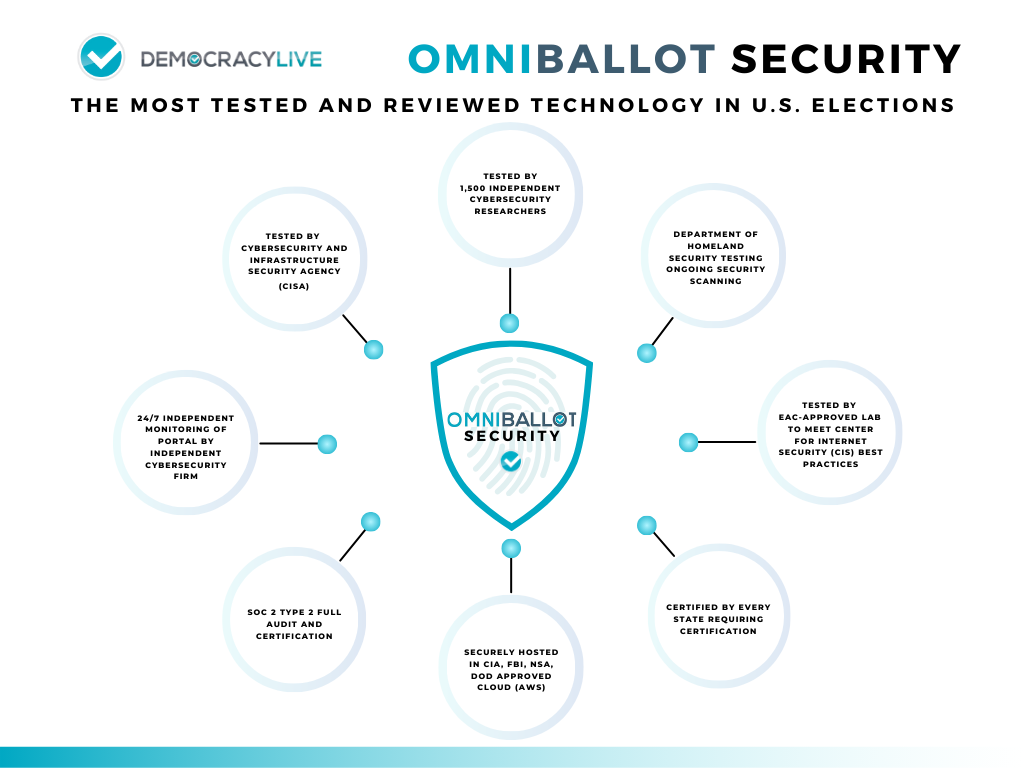
Implemented in over 5,000 elections, serving nearly 20 million voters, across 34 states the Democracy Live flagship product, OmniBallot, is the most independently reviewed technology in U.S. elections. In this section, we provide a high-level security overview of the steps Democracy Live takes to ensure OmniBallot is the most secure electronic ballot transmission tool in the nation.
Our Security Program
At Democracy Live, our primary responsibility is to protect and ensure the integrity of the voter’s ballot and our customer’s data. We do so by following Homeland Security, Department of Defense and the Center for Internet Security Best Practices for cloud-based solutions.
OmniBallot has been developed with a defense-in-depth architecture and are continuously improving by adopting proven and well-established cybersecurity tools. We consistently validate our adherence to these principles through 3rd party evaluations, monitoring and participation in federal programs such as the Department of Homeland Security Cyber-hygiene program and the federal Cybersecurity Infrastructure and the Security Agency (CISA) application and code review program. Democracy Live is the first elections technology in the nation to engage independent researchers to continuously test the system 24/7/365.
Enterprise OmniBallot Security
OmniBallot is hosted in Amazon Web Services (AWS) and has been architected according to AWS’s well-architected security pillar foundations. All environments are standardized, governed, and monitored to ensure real-time adherence to security and compliance requirements. This design allows for a highly available, rapidly scalable infrastructure with the following protections and capabilities.
Infrastructure Security
The following security mechanisms are in place within OmniBallot and AWS:
- Change Management – Defense against unapproved changes is ensured by using ControlTower, Organization level Service Control Policies (SCP) and Guard Rails. A change in security configuration within a customer account will be identified and remediated at an organization level.
- Automated Security Monitoring – Guard Duty is used to constantly monitor the AWS infrastructure for anomalous activity. Any findings trigger an alert through EventBridge allowing an administrator to quickly investigate using Detective.
- Centralized Logging – All logs are stored and protected in a central, isolated AWS account.
- Auditability – Every action performed in AWS is logged and immutably stored in AWS CloudTrail providing robust and reliable auditability.
- Best Practices – AWS environments are configured according to best practices from AWS, Center for Internet Security (CIS), and NIST frameworks.
- Encryption Everywhere – Comprehensive encryption for data in transit and at-rest.
- Automated Data Monitoring– All data storage locations are monitored continuously for unauthorized PII. Automated alerts are delivered if found.
- Vulnerability Scanning – Images and code are continuously scanned for vulnerabilities. Administrators are notified when vulnerabilities are found and are able to quickly remediate through a CI/CD process.
- 24x7x365 Monitoring – to monitor environment health and security with human eyes.
- Least Privilege and Separation of Duties Approach – Personnel access is controlled utilizing least privilege and separation of duties approaches. For example, if elevated access is needed, only employees with certain positions may be granted temporary credentials and only to specific AWS roles or environments based on what is needed.
- Business Continuity – OmniBallot resiliency utilizes many inherited AWS native features and managed services, such as zone redundancy, and data snapshots.
Application Security
- Frontline Defense – All application administration and/or voter interaction with OmniBallot is funneled to OmniBallot’s API and then routed through a Content Delivery Network (CDN) called AWS CloudFront which is protected by a web application firewall (WAF). This ensures consistent and reliable data flow through OmniBallot’s systems, performance improvements, and security against numerous types of application and infrastructure-based attacks.
- Best Practices – Democracy Live’s development team follows OWASP’s Top 10 and web application security best practices during development.
- Advanced User Security – Access to administrative applications is controlled by AWS Cognito with Advanced Security enabled. Cognito Advanced Security provides protections including MFA, adaptive authentication, bot detection, compromised credential detection, and risk analysis.
- Client-Side Application – OmniBallot is a single page application which allows voter selections to be maintained client side rather than having to store selections on a server through a session token in order to persist between page loads.
- Flexible Voter Authentication – OmniBallot utilizes a one-way hashing algorithm in order to securely store data provided by States or Counties. This provides a secure way of authenticating voters without storing sensitive information such as SSN, Driver’s License, or a voting PIN.
- Authenticity Checks – Each action performed by a voter is signed and validated using a JSON Web Token (JWT) to ensure future requests are valid and secure. These tokens are easily readable but provide built in encryption and validation to ensure they cannot be manipulated.
Electronic Ballot Transmission & Electronic Ballot Return
Electronic Ballot Transmission (EBT) provides an interface for voters to securely and electronically access, mark, review, print or return a ballot to their local elections official. For jurisdictions using the optional electronic ballot return (EBR) module, all ballots are reviewed by the voter before the ballot is printed. EBR is not an “online voting system”. OmniBallot has been designed to closely align with existing county processes for remote ballot transmission.
- Built in validation – EBR can be configured to require various validation components from voters (DL, SSN, PIN, MFA) depending on jurisdiction requirements.
- Immutable Storage – Ballots in EBR are stored using immutable file storage called Object Lock. These files cannot be modified or deleted until 90 days after an election.
- Ballot Preview/Verification – After storing the ballot in Object Lock, the voter is presented with the ballot to confirm it has been marked as intended. This verification happens before submitting their ballot. This allows the voter to validate their selections have not been manipulated in any way.
- Security Center – EBR includes a security dashboard allowing administrators to monitor ballot submission in aggregate and identify potentially suspicious submissions.
- Hash Validation – File hashes are stored within OmniBallot and are validated every time the file is viewed or downloaded by an administrator. This provides an additional mechanism to confirm the ballot has not been altered or corrupted in any way.
- Voter Privacy – Voter privacy is built into EBR by storing voter packages and ballots in entirely separate locations. If an Elections Official accesses a voter package during processing, they are not allowed to access the corresponding ballot. Similarly, if an Elections Official accesses a ballot, they cannot access the voter package. All access to these files is logged and clearly displayed within the administrative portal making access both identifiable and auditable. Files stored within AWS utilize random GUIDs with no connection between the voter package and ballot. Service Control Policies (SCPs) are defined at the organization level prohibiting direct access by developers or even administrators.
Policies and Procedures
Democracy Live has implemented numerous policies and procedures designed to guide personnel in the design, implementation, and execution of our security program. Policies are updated regularly to keep pace with changes in regulations, technologies, and industry best practices.
Risk Management
More than ever, Democracy Live recognizes that there is a rapidly evolving threat landscape that incessantly challenges our company’s growth against the need to balance customer’s business requirements. We are committed to ensuring that threat realization does not endanger the success of our customers. We maintain a robust Cyber Risk Management program to identify, prioritize and manage risks. We continuously perform risk assessments on our environments and products to evaluate current risks and ensure our controls are effectively managing those risks, including our vendors. We employ a proactive programmatic approach to our risk management, based on Carnegie Mellon’s OCTAVE FORTE framework, in which we evaluate the cost and effort of managing a threat with anticipated benefits, then mitigating those threats prior to risk realization.
Our program focuses on the following fundamentals:
- A commitment to the security, availability, confidentiality of Democracy Live infrastructure and services from senior management.
- The involvement, cooperation and insight of all Democracy Live employees.
- A commitment to initiating risk assessments, starting with discovery and identification of risks.
- A commitment to the thorough analysis of identified risks.
- A commitment to a strategy for remediation of identified risks.
- Risks transparency through open internal communication.
- A commitment to encourage the reporting of risks and threat vectors from all Democracy Live employees, customers, and the public.
Our program includes the following:
- Risk Registry
- Risk/Threat Library
- Risk Assessments
- Risk Mitigation
- Risk Monitoring
- Governance Committee
- Integration with other programs including Business Continuity (BC) and Disaster Recovery (DR)
- Employee Security Awareness Trainings
Incident Response
Democracy Live understands how an organization responds to an incident can have tremendous bearing on the ultimate impact of the incident. Our incident response planning, training, and testing is a critical component to our overall enterprise risk management program and risk reduction efforts. Furthermore, it incorporates best practices from NIST 800-61, NIMS, and NISTIR 8310 (NIST CSF). It is constructed to help ensure Democracy Live has an orderly, effective response to any type of incident.
Our program is a two-phased methodology based on NIST.
Phase I: Detection, Assessment, Containment – Evidence Collection, Analysis and Investigation.
Phase II: Remediation, Recovery – Post-Mortem, Notification.
Our plan focuses primarily on the following:
- Mitigate operational impact from incidents
- Reduce potential direct and indirect financial loss from focused intrusions
- Comply with regulatory and contractual requirements for cyber and physical security, in particular the protection of customer privacy
- Comply with Incident Response requirements and use industry best practices as published by the National Institute of Standards and Technology (NIST), and the National Infrastructure Protection Center as guidelines
- Provide detailed steps, roles, responsibilities, and direction on what to do when faced with an incident (SOPs)
Our plan is designed to act as a systematic script detailing required steps for both cyber and physical incidents. It includes the following:
- Approved tools and procedures
- Runbooks
- Communications
- Cyber Incident Response Team (CIRT)
- Notifications
- Standard Operating Procedures (SOPs)
- Call trees
- Postmortem report with root cause analysis
- Integration with other programs BC and DR
- Training
- Testing
Business Continuity (BC) and Disaster Recovery (DR)
At Democracy Live, we are deeply passionate about our country’s electoral process. We unequivocally believe that voters have the right to vote in a secure, accessible, and independent manner. Our BC and DR programs are shaped by the same drive that our elections must always occur. Our business revolves around the successful development and execution of OmniBallot. This not only entails application software development, but the supporting infrastructure that OmniBallot resides in, the personnel who develop the application and administer it, and the endpoint devices personnel use to perform said activities. We limit disruptions to our customers by solutions with built-in resiliency requirements capabilities. Furthermore, our programs contain contingencies designed for business processes, assets, and business partners (vendors).
Our programs focus on ensuring high availability and continuous operations for mission critical services by designing redundancy measures to meet customer RPO and RTO resiliency requirements, training and testing to minimize customer impacts, continuous monitoring to identify and detect potential issues early, and a continual view for improvement.
Our programs focus on the following fundamentals:
- Identify the activities, resources, and procedures needed to carry out Democracy Live’s processing requirements during prolonged interruptions to normal operations.
- Identify and define the impact of interruptions to Democracy Live’s systems.
- Assign responsibilities to designated personnel and provide guidance for recovering Democracy Live operations during prolonged periods of interruption to normal operations.
- Ensure coordination with other Democracy Live staff who will participate in the contingency planning strategies.
- Ensure coordination with external points of contact and vendors who will participate in the contingency planning strategies.
- Ensure quick, accurate, and transparent communications with our customers
Our programs include the following:
- Business Impact Assessment’s (BIA)
- Design principles
- Integration with other programs like Incident Response
- Runbooks
- Response team
- Training
- Testing
Certifications and Independent Security Reviews
Democracy Live undergoes an annual SOC 2 Type 2 attestation with trust services criteria relevant to Security, Availability, Process Integrity, Confidentiality, and Privacy.
Democracy Live’s OmniBallot application has been continuously analyzed and tested, year after year, by some of the world’s leading security experts. In all, there have been over seven significant independent reviews covering OmniBallot’s source code, functionality, and AWS supporting infrastructure since June 2020. Both black and white box tests have been conducted along with infrastructure scanning and application Function/Business Logic, Brute Force, and Authentication/Session Management to validate environment security hygiene.
24/7/365 Testing
Democracy Live appreciates the importance of penetration testing. We also understand that traditional penetration tests are typically point-in-time spot check evaluations that may become outdated as software improves and evolves over time. We consider a point-in-time testing process a risk. Our approach is to undergo continuous penetration testing. This is accomplished through a service called Synack365, performed by Synack, a recognized leader in cybersecurity and penetration testing. This service provides around-the-clock testing, real-time reporting, patch verification, and is supported by more than 1,500 security researchers. This means that OmniBallot’s current state and its supporting services are always being reviewed and tested.
